Child Protection on the Internet
Hear Kenn talk about Child Protection on the internet with Stuart George on Radio Stoke.
Hear Kenn talk about Child Protection on the internet with Stuart George on Radio Stoke.
Click to hear Kenn discussing reporting suspicion of terrorism on Radio Wales.

The Private Investigator has always been portrayed in the cinema as a charismatic dark, sometimes sinister figure and in the media as a 16 year old cyberpunk cracking foreign intelligence codes and now, of course, as a criminally minded social intruder and phone hacker.
Many see PI’s as a civilian spy, a one-man band trying to make a meagre living from day-to-day routine enquiries waiting in anticipation of the ‘big job’.
So what exactly is a private investigator? The ex-police officer serving papers from the court in divorce proceedings? The retired person whose sense of curiosity and justice stirs them into action? Or the slick, quick, industrial-espionage specialist who continually tries to foil and outwit unscrupulous business people who are bent on financial and political power? Or the PI working for them to bring power by information at any price?
The truth of it is that all of the above and many other definitions fit into the world of the modern day Sherlock Holmes. The type of work carried out by investigators is as diverse as the people who take up the profession. As well as the usual, widely accepted and well-known matrimonial and divorce work, the modern investigator can be called upon to act as a professional witness, involved in gathering evidence to support legal applications put before the court. Sometimes the PI will be called upon to work in criminal investigations to help prove a theft or some other crime, and to gather evidence to be given to the police as part of a court case being presented before a judge or passed to a journalist to expose a wrong-doing. On the other hand, the PI may have to work for the defence of a suspected criminal, meticulously sifting through the evidence and challenging any inconsistencies or locating and interviewing possible defence witnesses.
I’ve worked as an investigator for more than 30 years and I have been called upon to carry out investigations to locate and prove that firms or individuals are manufacturing or supplying goods without the license-holder’s consent. Retail and manufacturing companies have used the skills I learned as a soldier to work undercover or to carry out covert surveillance, gathering information to determine how their employees operate out of site of management, to identify individuals or teams involved in theft, using company equipment without consent or selling intellectual intelligence and testing the company’s security and systems. I have been deployed overseas working undercover to expose Letter-of-Credit fraud, child abduction and protection. I’ve lived in attics, under garden sheds, in disused properties, even in drains gathering video evidence to show that a claimant – although saying that he/she is unable to work – is in fact fit and healthy. I’ve met with Special Branch and handed information over to uncover future terrorists leaving the UK for training abroad.
I would argue that society will always have the need for information and in most cases the needy will not really care how that information was gained.
Defining piracy seems at first glance to be a simple process but for the sake of intelligence gathering a more precise definition is needed especially when the information received could lead to the deployment of special operations groups to an area where in fact there has not been a properly defined recordable incident, leaving dangerous areas without adequate cover. The problem, of course, is one of the master’s experience and recent knowledge and analysis.
It is easy to make a mistake and to believe, and consequently, report an ‘incident’ when in fact the observed action was not what it first appeared to be. Large numbers of legitimate fishing vessels operate in the Southern Red Sea and many of these fishing vessels approach merchant ships either to improve their fishing or to warn ships away from their nets.
Keeping up to date with local intelligence is the best way to avoid unnecessary panic. Knowledge, as they say, dispels fear. Knowing that in the northern Somali Basin the preferred mother ships are usually local dhows and that in the southern Somali Basin the use of 8 metre whalers are used does give the master a definite advantage. Obviously these are not hard and fast rules and that is exactly why quantified and qualified regular information is needed to inform the intelligence services, such as United Kingdom Marine Trade Operations (UK MTO) who in turn will publish Best Management Practices (BMP) ensuring that everyone can benefit and contribute to everyone’s safety.
Piracy Definitions are set out in BMP 4 and in essence defining what is a Piracy attack and what is deemed to be a suspicious activity:
‘A piracy attack may include, (but is not limited to), actions such as the following:
• The use of violence against the ship or its personnel, or any attempt to use violence.
• Attempt(s) to board the vessel where the Master suspects the persons are pirates.
• An actual boarding whether successful in gaining control of the vessel or not.
• Attempts to overcome the Ship Protection Measures by the use of ladders, grappling hooks or weapons deliberately used against or at the vessel.Pirate Attack – is where a vessel has been subjected to an aggressive approach by a pirate craft, AND weapons have been discharged.Hijack – is where pirates having boarded and taken control of a vessel against the crews will.
Illegal Boarding – is where pirates have boarded a vessel but HAVE NOT taken control. Command remains with the Master. An obvious example of this is the Citadel scenario.
Suspicious or Aggressive Approach – includes action taken by another craft which may be deemed suspicious if any of the following occur (the list is not exhaustive):
• A definite course alteration towards the craft associated with a rapid increase in speed, by the suspected craft, which cannot be accounted for as normal activity in the circumstances prevailing in the area.
• Small craft sailing on the same course and speed for an uncommon period and distance, not in keeping with normal fishing, or other circumstances prevailing in the area.
• Sudden changes in course towards the vessel and aggressive behaviour.
Guidance Note:
In helping to evaluate suspicious activity, the following may be of assistance to determine the nature of a suspect vessel:
• The number of crew on board relative to its size.
• The Closest Point of Approach (CPA).
• The existence of unusual and non-fishing equipment, e.g. ladders, climbing hooks or large amounts of fuel on board.
• If the craft is armed in excess of the level commonly experienced in the area.
• If weapons are fired in the air.’
For the sake of completeness the following UK MTO advice is recommended:
‘Prudent and timely application of BMP can make the important difference of being approached, attacked, or being pirated. If any incident occurs, Masters are requested to report immediately to UKMTO via telephone and provide the details of the incident. This will ensure the information is provided to other ships in the area for their awareness and vigilance. If Masters are safely able to take pictures and/or video of the suspicious activity, please provide these via email to UKMTO (ukmto@eim.ae), the NATO Shipping Centre (info@shipping.nato.int) and MSCHOA (postmaster@mschoa.org).’
And…
‘Vessels are strongly encouraged to report any suspicious sightings or aggressive approaches to UKMTO via telephone (+971 505 523 215). This will allow maximum opportunity for appropriate advice and assistance. Vessels are asked to follow this up with an email report and any photographs available as soon as possible after the incident.’
This book could save your life.
You can curl up under a table or you can react in a calm, clear manner and dramatically increase your chances of survival in a variety of extreme situations.
This book covers all the basics – fire-fighting, shelter-building, water-collection – as well as many other important skills needed to survive the unfortunate events that can occur in daily life.
Written by expert Kenn Griffiths, a former soldier and private investigator who worked all around the world. He is skilled in survival techniques, as well as in anti-terrorism and covert surveillance.
Click below to watch Kenn on Victoria Derbyshire programme talking about drone attacks.
https://www.bbc.co.uk/iplayer/episode/b0bvll7m/victoria-derbyshire-20122018
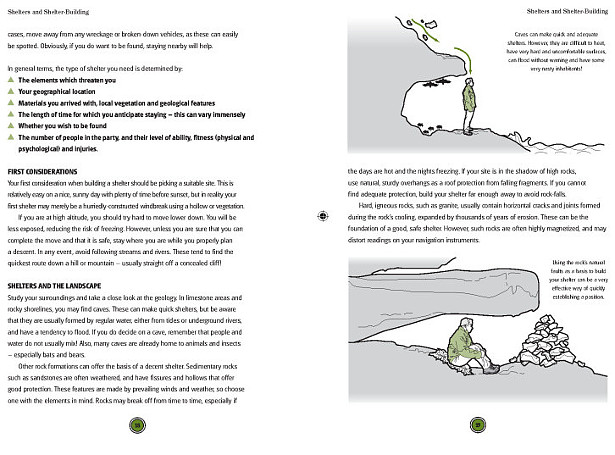
What if you were left stranded after an avalanche, or dropped into the middle of a jungle, shipwrecked on an island, or found yourself alone on a deserted street in the middle of a strange city – could you cope?
World events have changed our perspective on many things, and proved that even in an age when technology can make life simple, we still need our inner strength and ability to survive day by day. The Essential Survival Guide not only explains how we can develop the right psychological approach to cope with extraordinary and life-threatening situations, but also provides information on the methods and practical techniques that can determine whether you live or die – from basic self-defence to finding food and shelter.
No matter where you may go or what you may do, ask yourself one question: do you have the know- how and the will to survive? If not, you need this book.
As a former British soldier, private investigator, undercover operator and police special constable Kenn has first hand experience of survival, anti-terrorist and covert surveillance techniques. As a soldier he served in many remote areas of the world and his knowledge and research have given him an invaluable insight into a world which most of us will never see but which he shares with a writers passion.
Kenn has authored many books including The Private Investigator’s Handbook and The Essential Survival Manual.
Kenn was invited to give a hands on survival talk and book signing session at Mostly Books, New Bookshop of the Year 2008, in the Thameside market town of Abingdon, Oxfordshire.

Ever since we set the event up, I was unfeasibly excited about last Tuesday’s “Survival” event with Kenn Griffiths. I’m pleased to say it met all my expectations – and more. A really great event. The shop still smells (faintly) of wood smoke, but the parachute-covered shelter is now down, and lots of children in and around Abingdon now have a better idea on a whole range of subjects – from knowing the best way to light a fire to concealing themselves in foliage – and even the dangers (and best way) of drinking your own wee….
Yes – this was “Survival” at Mostly Books!
Taken from the Mostly Books! Blog. To read the full account of Kenn’s visit: Kenn Griffiths at Mostly Books!


From escaping from a sunken vehicle to navigating by the stars, from self defence to lighting a fire and administering first-aid this book offers a wealth of indispensable knowledge for every reader including:
The mindset to win (psychology of self-defence)
Protection (shelter, water, fire)
Location (map and compass, search and rescue, attracting attention)
Water (solar stills, locating and purifying)
Food (fires, cooking traps)
Surviving People (on foot, transport, natural disaster)
Self-help
First-aid
List of the world’s danger spots
Kenn Griffiths Author and Writer credits include;
Books: Usborne Survival Skills, The Private Eye’s Handbook, The Private Investigator’s Handbook, Spy Master, The Essential Survival Guide, Map and Compass, The Survival Manual.
Magazines: The Royal Geographical Magazine, Survival Weaponry and Tactics Magazine, Countryside Magazine, Why! Army Benevolent Fund Magazine, Daily Agony Column Expert for Inside Divorce E-Magazine.